Ever since the launch of Office 365 (and BPOS before that) there has been a desire to make accessing these services as seamless as possible. Single Sign On (SSO) has long been high on the requirements list for many organizations and while it has been possible for some time now to provide a near seamless login experience, it has historically come at a cost in the form of additional infrastructure - usually deployed on-premises and at the very least carrying some sort of administrative burden. I’m not against identity federation, I think it definitely has it’s place and most of the customers I work with already have some federation solution deployed so it makes a lot of sense leveraging it for Office 365 as well, but there are always those organizations who don’t already have a solution in place or those smaller environments where it doesn’t make a whole lot of sense to implement a highly-available AD FS deployment.
Password Sync has long been the best compromise, offering a “Same Sign On” experience where users are able to use their existing AD credentials to access Office 365 services. The recent announcement of Pass-Through Authentication and Single Sign-on means that things are about to get a whole lot better!
I wanted to put together a quick post and run through how easy it is to setup Single Sign On and review the user experience when it is used with Password Sync. Single Sign On can also be enabled with the new Pass-through authentication option, but that’s a story for another post!
Before getting started, it is important to understand the client requirements. The client should:
- be using a domain-joined machine
- be using Windows and a supported browser (Edge is not supported)
- have direct access to a domain controller
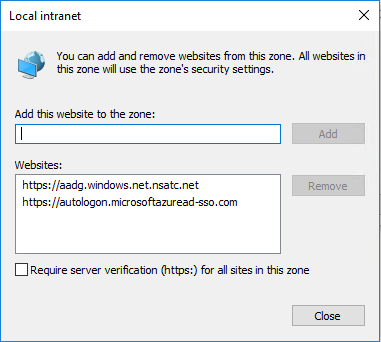
- have the Kerberos end-points defined in the browser’s Intranet zone (AD Group Policy is the easiest way to do this)
- https://autologon.microsoftazuread-sso.com
- https://aadg.windows.net.nsatc.net
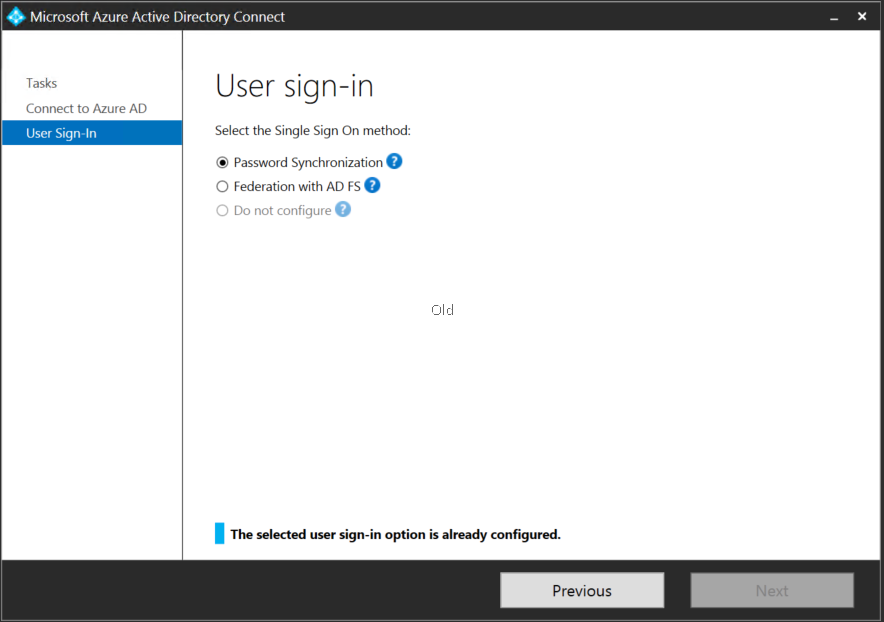
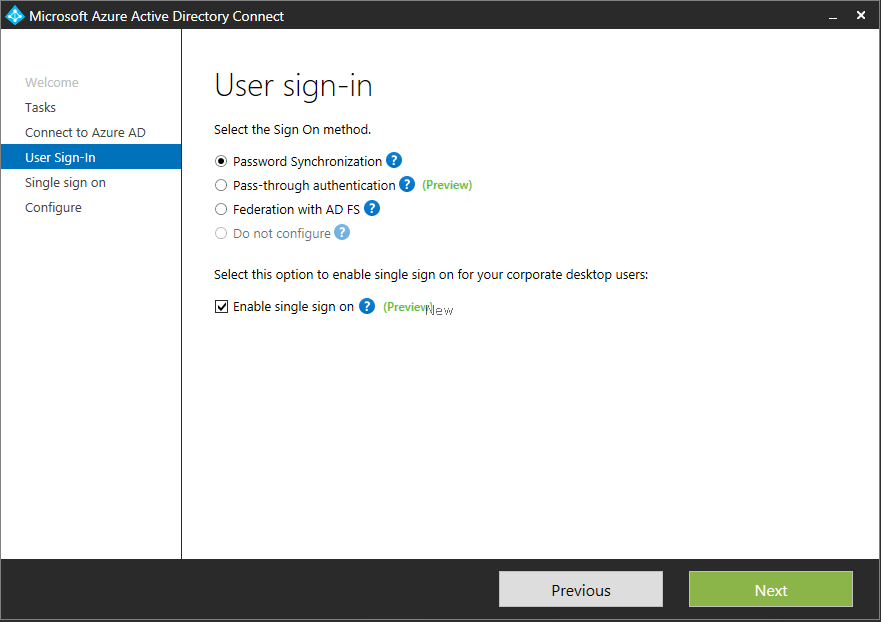
Once the client requirements have been taken care of, we need to update AAD Connect. At the time of writing, version 1.1.380.0 is the latest version. It looks like these new features were introduced in version 1.1.370.0. If we compare the the “User sign-in” page to that of an older build you’ll notice the addition of a few more features:
To upgrade AAD Connect, follow your regular upgrade procedure. If you don’t have any customizations or special considerations, you can just let the wizard perform the upgrade for you:
Once upgraded, you’ll want to run the configuration wizard again and tick the “Enable single sign on” checkbox on the “User sign-in” page (shown above) and that is all there is to it!
Let’s compare the user experience before and after enabling Single Sign On. Here is the user experience before:
and here is the user experience after implementing Single Sign On with AAD Connect (you’ll notice that I do not have to re-enter my password this time):
Note: In the demo videos, I have my home page set in a way that forces my custom branding before any user credentials are entered. You can do this by either creating a web redirect or setting your home page to: https://login.microsoftonline.com/login.srf?whr=your_domain.com (replace your_domain.com with your actual domain name!)
There is a lot of great documentation available about Single Sign On on the Microsoft website, I highly recommend that you check it out as well: