Azure Active Directory (AAD) conditional access is something I’ve been wanting to post about for a while now. A scenario I come across fairly often is the desire to prevent access or add an additional layer of security to certain Office 365 workloads when the user is connecting from a remote, non-corporate location. In the past, this could be achieved by making use of claims rules and Active Directory Federation Services (AD FS) which meant that it wasn’t possible for those organizations not making use of federated identities with Office 365.
AAD conditional access solves this problem and makes it really simple to apply access policies to AAD connected applications. Conditional access does require an AAD premium license (P1). In this post we’ll cover a simple location based scenario where we prevent users from accessing Outlook on the web (OWA) from outside of the organization’s network. In order to configure conditional access you will require:
- Azure Active Directory premium licensing
- Access to the Azure management portal (classic portal)
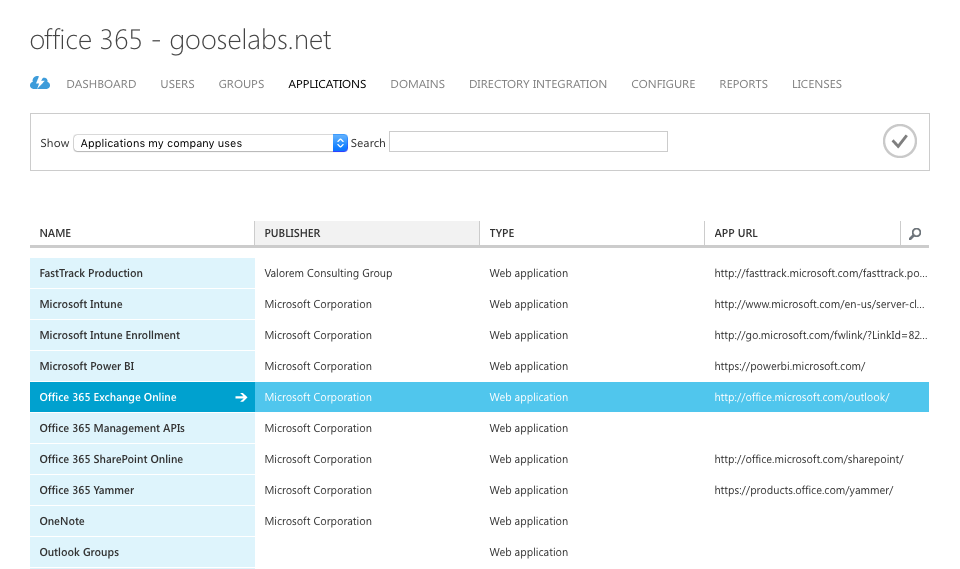
Conditional access policies are configured via the classic Azure management portal (http://manage.windowsazure.com). Locate “Active Directory” on the left-hand side, select your Office 365 directory and click the “Applications” option.
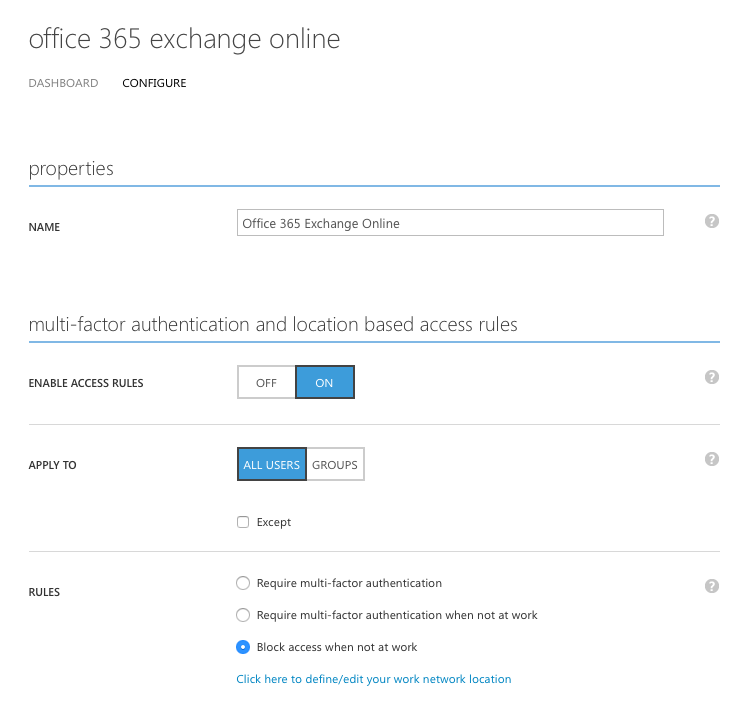
Next, select the “Office 365 Exchange Online” application and turn access rules “On” under the “Multi-factor authentication and location based access rules” section. You have the option of applying your rules to all users or select groups. You then select the “Block access when not at work” option. You also have to option to enforce MFA for an application which is useful if you would like to enable MFA only for specific applications or you could require MFA only when users are accessing the application from outside the corporate network.
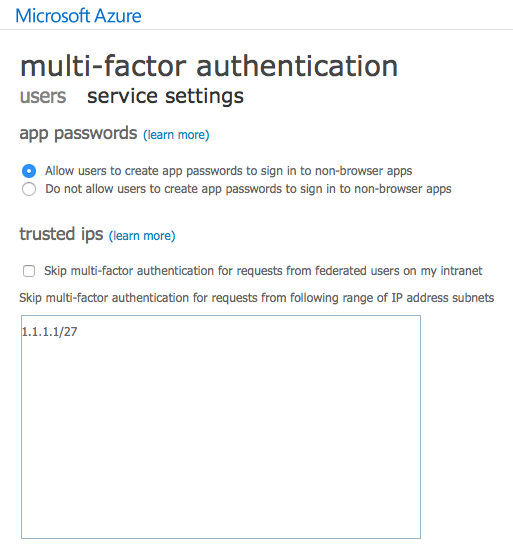
It is important to ensure that you define your corporate network ranges by clicking link. All connections from locations outside the definted network ranges will be treated as remote.
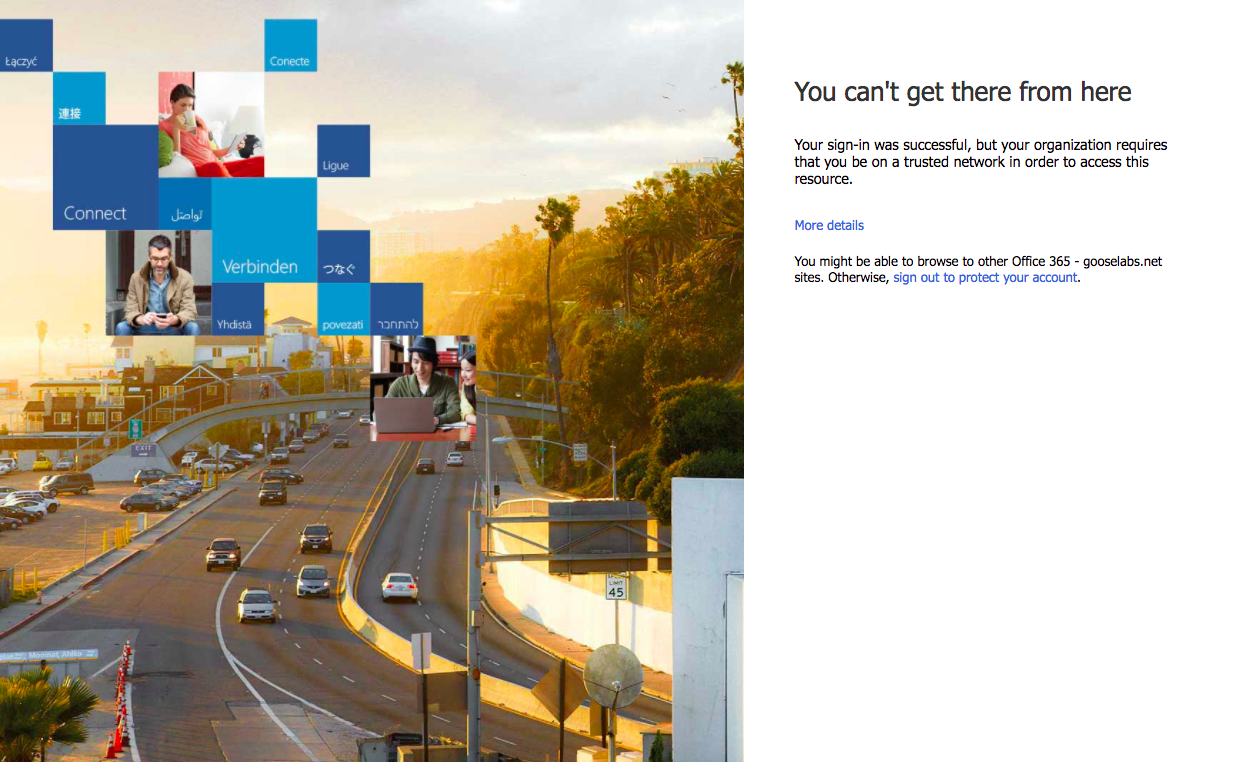
 Once configured, you will notice that users are still able to access the Office 365 portal however, once they click the mail option in the app launcher they will no longer be able to access Outlook on the web unless they are connecting from a approved location.
Once configured, you will notice that users are still able to access the Office 365 portal however, once they click the mail option in the app launcher they will no longer be able to access Outlook on the web unless they are connecting from a approved location.
This is a very simple example of how to use location based access rules. It is also possible to configure device based access policies which provide an incredible amount of control over which devices can access your applications. I’ll cover device based access policies in a future post.