I am often surprised by how few customers know about or use ActiveSync device access rules (or ABQ for short) in Exchange 2010 when everyone seems to have the requirement to some degree or another. I see a growing trend to use third party products to do what Exchange can and has been able to do natively for a while now so I thought I would put together this post to go through some of the functionality offered by ABQ.
Before I continue, I would like to highlight the following two things:
- Device access rules (ABQ) should not be confused with or is not intended to replace ActiveSync policies which are used to enforce things like device passwords, device encryption, etc. (click here for more on ActiveSync policies)
- Everything described in this post also applies to Exchange Online
Depending on your requirements, you may decide to take a restrictive approach where you only allow a small set of tested and supported devices or be more permissive and only block/quarantine problematic devices. For this post, I will create a device policy to quarantine any iPad devices. The use case for this scenario is that an organisation may for example allow users to choose whatever mobile phone they would like to use but block the use of iPads because these are not devices issued by the company. By quarantining a device, we can easily see who is attempting to use such a device, how many are out there and even decide to create a new policy specific to these devices.
During the connection process, Exchange will follow a logical set of rules to determine the access state of each device and will either allow, block or quarantine the device based on the outcome. The sequence of challenges includes the following steps:
- Is the device authenticated? If not, challenge for the correct credentials. Otherwise, go on to the next step.
- Is Exchange ActiveSync enabled for the current user? If not, return an "access restricted" error to the device. Otherwise, go on to the next step.
- Are the policy enforcement criteria met by the current mobile device? If not, block access. Otherwise, go on to the next step.
- Is this device blocked by a personal exemption for the user? If so, block access. Otherwise, go on to the next step.
- Is this device allowed by a personal exemption for the user? If so, grant full access. Otherwise, go on to the next step.
- Is this device blocked by a device access rule? If so, block access. Otherwise, go on to the next step.
- Is this device quarantined by a device access rule? If so, quarantine the device. Otherwise, go on to the next step.
- Is this device allowed by a device access rule? If so, grant full access. Otherwise, go on to the next step.
- Apply the default access state per the Exchange ActiveSync organisational settings.
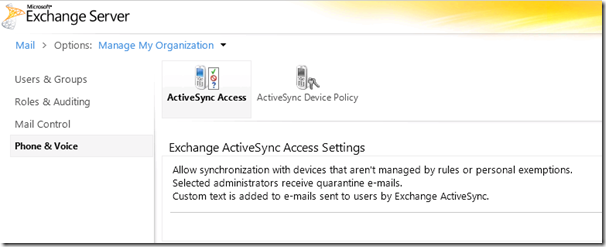
The device policy that I am going to create will be applied at Step 7. To create a device policy, we need to access the “ActiveSync Access” options under “Phone & Voice” settings in the ECP. It should look something like this:
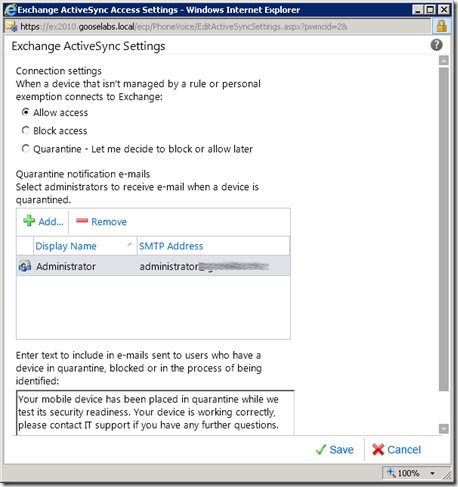
Clicking the “Edit” button will allow you to edit various settings. As you can see, I have decided to be permissive and allow all devices unless they are managed by a rule. You can select a distribution group or administrative account that will receive quarantine notification emails. You also have the option to add any custom or organisation specific text that will be included in the email notification sent to users when their device is blocked or quarantined.
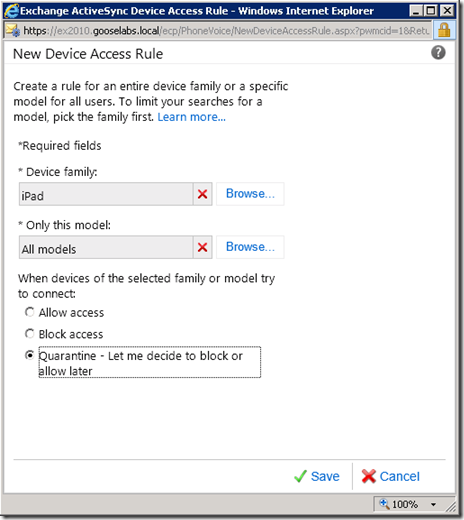
We then click “New” under “Device Access Rules” at the bottom of the page to define our new rule. Here we can browse a list of all the devices and device families that have recently connected to our Exchange environment. Device family is a grouping of similar devices, in our case for example if we choose a Device family of “iPad” we can then decide to only apply this rule to iPad2 models or “All models” by selecting the appropriate device type. Lastly, we select our ABQ action.
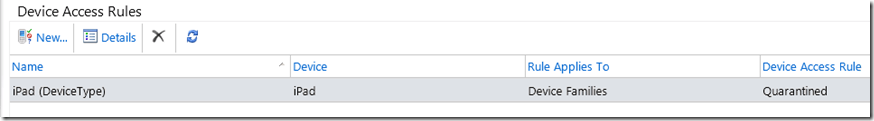
Once we have clicked “Save” we should see the new device access rule listed under “Device Access Rules”
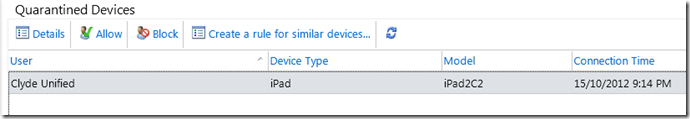
Once we have created the access rule, if any users attempt to connect using an iPad, they will be listed under “Quarantines Devices”
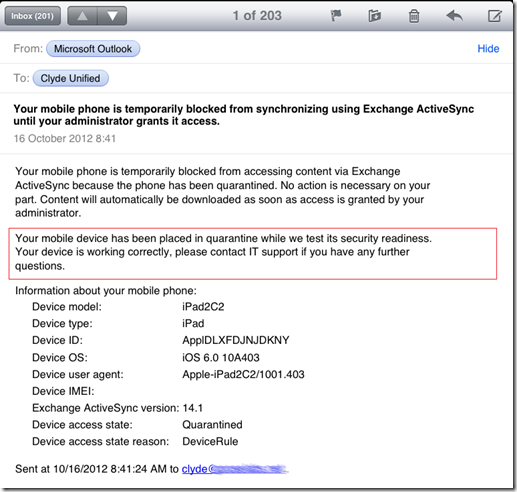
Users will receive a notification email similar to the following if they try to connect using an iPad. Note the custom text entered previously (red box)
One last thing to mention is that you do have the ability to make a personal exception for a specific user if needed, so for example if you have an executive who is adamant about wanting to use his/her iPad of if you decide after some time to test iPads this can be done without affecting anyone else. As always, full documentation can be found on TechNet